aDevelop Secure Development Platform
Version 1.3 2013-11-01
Schematic
Description
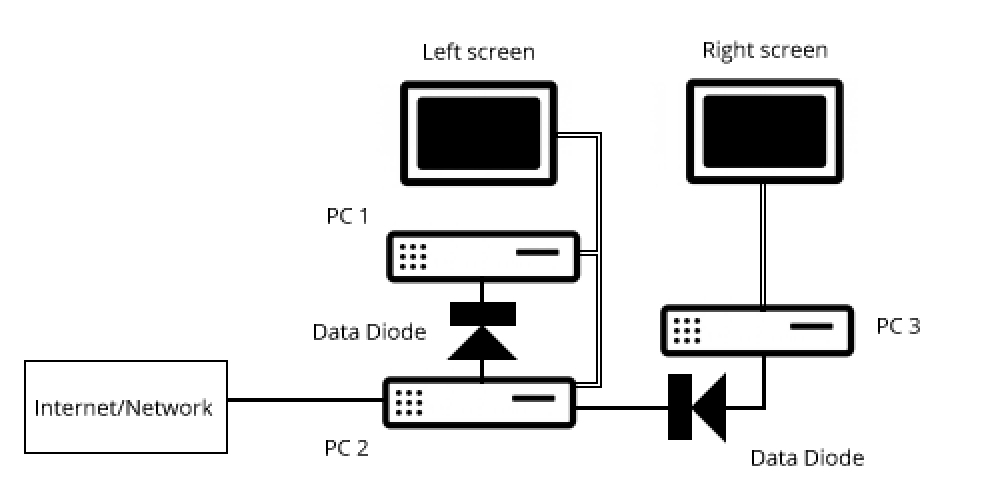
Our workstations consist of three separate PC’s and two screens. (Screen includes keyboard, mouse, etc.)
The left screen is considered ‘dirty’, the right screen ‘clean’.
The right screen is connected to PC3.
PC3 is not connected to any network and contains only the absolute minimum development software necessary for the clients app. This software is loaded from the manufacturer’s disks.
PC2 is connected to the internet, with the latest malware protection installed, along with any other downloaded auxiliary software the developer may need.
PC1 is the test environment for the customer’s app, along with any other downloaded auxiliary software the developer may need.
The left screen can be toggled between PC1 and PC2.
A data diode is a network connection that only allows data to flow in the direction of the arrow. Those used are a hardware implementation.
PC1 and PC3 have no USB sockets, CD/DVD drive, WIFI or other means of connection.
Use
The developer receives encrypted emails/work from the client /GIT on PC 2. These are copied via the data diode to PC1 and decrypted there. Tests of any data sent may be run against the test environment.
In the event of a software change, the developer uses the right screen. When the change has been made, the module(s) are encrypted and transferred via data diode and PC2 to to the test environment, PC1, for testing.
When testing is complete, the encrypted modules on PC2 are emailed to the customer for installation on their servers.
Explanation
The developer station PC3 is completely isolated from all incoming malware. The only real risks are malware on the manufacturer’s disks, created by the developer, or sent by the customer.
PC1 and PC2 are only protected by the malware protection software, so must be considered insecure. The data diode does mean, however, that decrypted customer data and modules on PC1 is totally inaccessible and cannot be attacked.
All customer modules and data on PC2 are encrypted and signed, so, depending on the encryption used, can be seen as being secure.
Encryption/Decryption keys reside only on PC1 and PC3, so are totally inaccessible to attackers.
.